Share this
Mini Guide to Content Protection
by THEO Technologies on December 24, 2019
With piracy on the rise again, it is worth taking a moment to consider how you can prevent your content from being pirated. Pirated content (ranging from link sharing to straight-out downloading of content) generally results in a loss of revenue. While there are many approaches to protect your content, each approach has its pros and cons, technical complexity and cost.
.png?width=680&height=355&name=EZDRM%20blog%20banner%20(15).png)
RESTRICTING CONTENT ACCESS
Restricting the access to your content is a fairly simple
and straight-forward approach to avoid your
infrastructure and content being abused. There are different approaches which can be taken for this, which often are very cost effective.
- Stream Tokenisation
- Cookies and/or browser sessions
- Geo-blocking
Stream Tokenisation
Stream tokenisation is a fairly common approach, as several CDNs and servers provide it out of the box. This system is based on access control, as the client will receive a token that allows to access the content through the download of a link. If the link to that video stream is copied, the client cannot access the stream. Most vendors provide solutions which work like this, where a token (for example a JSON Web Token) can be requested on the platform, and then used by a viewer to gain temporary access to a stream.
Cookies and/or Browser Sessions
Cookies and/or browser sessions can also be used in order to restrict access to content. Often this approach is more suited to be used only on manifest files or similar master files as it can be quite intensive for authentication systems which are not scaled for this.
Geo-blocking
An approach to restrict access within certain geographic areas is geo-blocking. This approach detects the location of the viewer based on information such as the user’s IP address and determines if their location is within the allowed area. An alternative solution could be to restrict the content access only on certain networks, for example within the campus of a university, or on a company network.
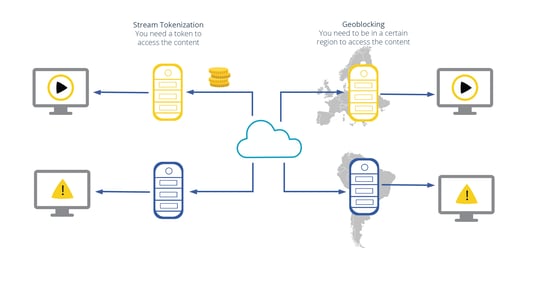
Example of stream tokenisation and geo-blocking.
Both stream tokenisation and geo-blocking are very suited as lightweight access restrictions. They can be used to avoid link sharing, and deterring people from using your streaming infrastructure to spread the content. While the approach does not make it extremely difficult to copy the actual content, it can provide an initial barrier for less tech-savvy people.
Content encryption AES-128
The most popular method for content protection is AES encryption. AES encryption is used in combination with all popular streaming protocols and is also the basis of a lot of DRM systems. The approach can be fairly inexpensive as there are a wide range of standard capabilities in streaming servers and tools. AES uses a key to encrypt and decrypt the content. In order to do so, both the sender and the receiver need to know the key.
Although AES is a hard to crack encryption schema, the weakest point in the system is key retrieval: once a key is known, it can always be used to decrypt (a part of) a piece of content. How this is done will depend on the streaming protocol used in tandem with the encryption.
HLS provides AES-128, which simply links the key in the manifest, while DASH is commonly used with the ClearKey encryption scheme. It is important to restrict access to the key itself by means of tokenisation or cookie/session-based access.
The AES approach, in combination with tokenisation, is a sound choice for everyone not being contractually forced by content owners to leverage full blown DRM solutions. It can be used to provide a high-grade protection without the cost of a DRM system and can provide a great challenge for even tech-savvy users.
DIGITAL RIGHTs management (DRM)
Encryption is also the basis of DRM systems. So, what makes a DRM system more secure?
There are two things to consider:
- DRM systems are set up so the key to decrypt content is never accessible. Instead, a license is shared, which is used by proprietary pieces of software to extract the key and decrypt the content.
- On top of that, most DRM implementations these days are hardware implementations, meaning decryption happens within the chipset itself, and no content can leak outside of a secure container. There are even measures in place to avoid automatic screen recording. These DRMs are often platform specific, such as Google’s Widevine on Android platforms, Microsoft’s PlayReady and Apple’s Fairplay.
Full DRM solutions are often enforced by content owners, especially for HD and 4K content. While there are some cases where DRM is also used for corporate or other high value content, it is often seen as an expensive solution.
HOW DRM WORKS
The image below depicts a simplified video streaming infrastructure, illustrating how DRM works. The process starts by first transcoding and encrypting the source content, in our case the video content. A copy of the encrypted content is sent to the CDN and the License Server. The CDN then stores and distributes the encrypted video fragments to the Video Player. In order to do anything with that content, the Video Player will need to communicate with the License Server to obtain the Decryption Key. The decryption keys only get communicated through a secure channel within the DRM Licence Server. A decryption key will never leave the DRM component.
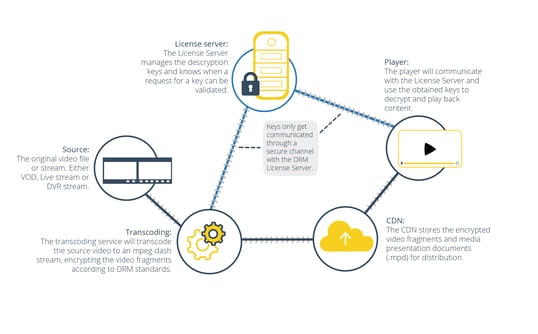
Deterring Piracy
While you can join the battle and fight piracy by making it more difficult to access, we also see an increase in the alternative approach: making your content easily available on your platform.
By delivering a compelling user experience and pricing model, users can be persuaded to return to your platform, instead of illegally downloading it from an obscure website. By leveraging a reasonable pricing scheme, or an advertisement approach which is not too obtrusive, in combination with features for content discovery, viewers can be persuaded to sign up and return to your portal.
Any questions left? Contact our THEO experts.
Share this
- THEOplayer (46)
- online streaming (40)
- live streaming (35)
- low latency (32)
- video streaming (32)
- HESP (24)
- HLS (21)
- new features (21)
- THEO Technologies (20)
- SDK (19)
- THEOlive (17)
- best video player (17)
- cross-platform (16)
- html5 player (16)
- LL-HLS (15)
- online video (15)
- SmartTV (12)
- delivering content (12)
- MPEG-DASH (11)
- Tizen (11)
- latency (11)
- partnership (11)
- Samsung (10)
- awards (10)
- content monetisation (10)
- innovation (10)
- Big Screen (9)
- CDN (9)
- High Efficiency Streaming Protocol (9)
- fast zapping (9)
- video codec (9)
- SSAI (8)
- Ultra Low Latency (8)
- WebOS (8)
- advertising (8)
- viewers expercience (8)
- "content delivery" (7)
- Adobe flash (7)
- LG (7)
- Online Advertising (7)
- Streaming Media Readers' Choice Awards (7)
- html5 (7)
- low bandwidth (7)
- Apple (6)
- CMAF (6)
- Efficiency (6)
- Events (6)
- drm (6)
- interactive video (6)
- sports streaming (6)
- video content (6)
- viewer experience (6)
- ABR (5)
- Bandwidth Usage (5)
- Deloitte (5)
- HTTP (5)
- ad revenue (5)
- adaptive bitrate (5)
- nomination (5)
- reduce buffering (5)
- release (5)
- roku (5)
- sports betting (5)
- video monetization (5)
- AV1 (4)
- DVR (4)
- Encoding (4)
- THEO Technologies Partner Success Team (4)
- Update (4)
- case study (4)
- client-side ad insertion (4)
- content encryption (4)
- content protection (4)
- fast 50 (4)
- google (4)
- monetization (4)
- nab show (4)
- streaming media west (4)
- support matrix (4)
- AES-128 (3)
- Chrome (3)
- Cost Efficient (3)
- H.265 (3)
- HESP Alliance (3)
- HEVC (3)
- IBC (3)
- IBC trade show (3)
- React Native SDK (3)
- THEOplayer Partner Success Team (3)
- VMAP (3)
- VOD (3)
- Year Award (3)
- content integration (3)
- customer case (3)
- customise feature (3)
- dynamic ad insertion (3)
- scalable (3)
- server-side ad insertion (3)
- video (3)
- video trends (3)
- webRTC (3)
- "network api" (2)
- Amino Technologies (2)
- Android TV (2)
- CSI Awards (2)
- Encryption (2)
- FireTV (2)
- H.264 (2)
- LHLS (2)
- LL-DASH (2)
- MPEG (2)
- Microsoft Silverlight (2)
- NAB (2)
- OMID (2)
- Press Release (2)
- React Native (2)
- Start-Up Times (2)
- UI (2)
- VAST (2)
- VP9 (2)
- VPAID (2)
- VPAID2.0 (2)
- ad block detection (2)
- ad blocking (2)
- adobe (2)
- ads in HTML5 (2)
- analytics (2)
- android (2)
- captions (2)
- chromecast (2)
- chromecast support (2)
- clipping (2)
- closed captions (2)
- deloitte rising star (2)
- fast500 (2)
- frame accurate clipping (2)
- frame accurate seeking (2)
- metadata (2)
- multiple audio (2)
- playback speed (2)
- plugin-free (2)
- pricing (2)
- seamless transition (2)
- server-side ad replacement (2)
- subtitles (2)
- video publishers (2)
- viewer engagement (2)
- wowza (2)
- "smooth playback" (1)
- 360 Video (1)
- AOM (1)
- API (1)
- BVE (1)
- Best of Show (1)
- CEA-608 (1)
- CEA-708 (1)
- CORS (1)
- DIY (1)
- Edge (1)
- FCC (1)
- HLS stream (1)
- Hudl (1)
- LCEVC (1)
- Microsoft Azure Media Services (1)
- Monoscopic (1)
- NAB Show 2016 (1)
- NPM (1)
- NetOn.Live (1)
- OTT (1)
- Periscope (1)
- Real-time (1)
- SGAI (1)
- SIMID (1)
- Scale Up of the Year award (1)
- Seeking (1)
- Stereoscopic (1)
- Swisscom (1)
- TVB Europe (1)
- Tech Startup Day (1)
- Telenet (1)
- Uncategorized (1)
- University of Manitoba (1)
- User Interface (1)
- VR (1)
- VR180 (1)
- Vivaldi support (1)
- Vualto (1)
- adblock detection (1)
- apple tv (1)
- audio (1)
- autoplay (1)
- cloud (1)
- company news (1)
- facebook html5 (1)
- faster ABR (1)
- fmp4 (1)
- hiring (1)
- iGameMedia (1)
- iOS (1)
- iOS SDK (1)
- iPadOS (1)
- id3 (1)
- language localisation (1)
- micro moments (1)
- mobile ad (1)
- nagasoft (1)
- new web browser (1)
- offline playback (1)
- preloading (1)
- program-date-time (1)
- server-guided ad insertion (1)
- stream problems (1)
- streaming media east (1)
- support organization (1)
- thumbnails (1)
- use case (1)
- video clipping (1)
- video recording (1)
- video trends in 2016 (1)
- visibility (1)
- vulnerabilities (1)
- zero-day exploit (1)
- November 2024 (1)
- August 2024 (1)
- July 2024 (1)
- January 2024 (1)
- December 2023 (2)
- September 2023 (1)
- July 2023 (2)
- June 2023 (1)
- April 2023 (4)
- March 2023 (2)
- December 2022 (1)
- September 2022 (4)
- July 2022 (2)
- June 2022 (3)
- April 2022 (3)
- March 2022 (1)
- February 2022 (1)
- January 2022 (1)
- November 2021 (1)
- October 2021 (3)
- September 2021 (3)
- August 2021 (1)
- July 2021 (1)
- June 2021 (1)
- May 2021 (8)
- April 2021 (4)
- March 2021 (6)
- February 2021 (10)
- January 2021 (4)
- December 2020 (1)
- November 2020 (1)
- October 2020 (1)
- September 2020 (3)
- August 2020 (1)
- July 2020 (3)
- June 2020 (3)
- May 2020 (1)
- April 2020 (3)
- March 2020 (4)
- February 2020 (1)
- January 2020 (3)
- December 2019 (4)
- November 2019 (4)
- October 2019 (1)
- September 2019 (4)
- August 2019 (2)
- June 2019 (1)
- December 2018 (1)
- November 2018 (3)
- October 2018 (1)
- August 2018 (4)
- July 2018 (2)
- June 2018 (2)
- April 2018 (1)
- March 2018 (3)
- February 2018 (2)
- January 2018 (2)
- December 2017 (1)
- November 2017 (1)
- October 2017 (1)
- September 2017 (2)
- August 2017 (3)
- May 2017 (3)
- April 2017 (1)
- March 2017 (1)
- February 2017 (1)
- December 2016 (1)
- November 2016 (3)
- October 2016 (2)
- September 2016 (4)
- August 2016 (3)
- July 2016 (1)
- May 2016 (2)
- April 2016 (4)
- March 2016 (2)
- February 2016 (4)
- January 2016 (2)
- December 2015 (1)
- November 2015 (2)
- October 2015 (5)
- August 2015 (3)
- July 2015 (1)
- May 2015 (1)
- March 2015 (2)
- January 2015 (2)
- September 2014 (1)
- August 2014 (1)

